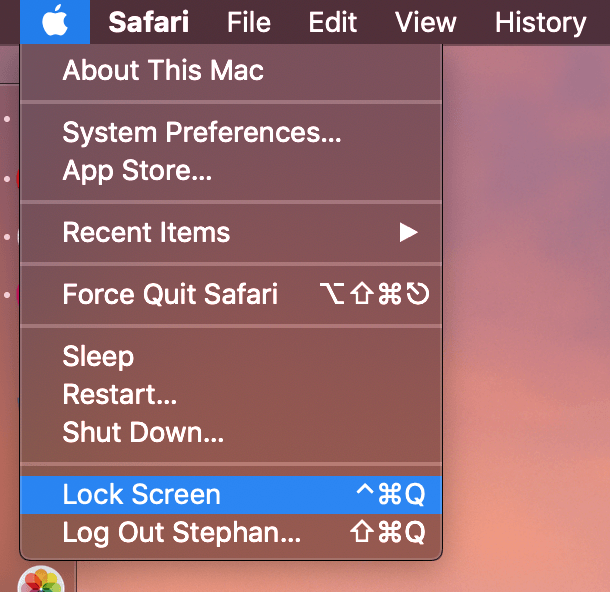
How can you quickly secure your Mac? A dedicated shortcut for locking the screen is paramount for security.
A keyboard shortcut, often a combination of keys, designed to activate the screen-locking feature on macOS. This action typically involves minimizing open applications, obscuring the desktop, and potentially requiring a password for unlocking. Examples include pressing Command + Control + Q (depending on the macOS version) to lock the screen, or employing a specific key combination like Command + Shift + Eject to lock the desktop without requiring a password for immediate use, depending on macOS settings. The exact shortcut employed might differ depending on the version of macOS being used.
This screen-locking function is vital for safeguarding sensitive information. By quickly locking the screen, a user prevents unauthorized access and potential data breaches. It's particularly valuable in shared or public environments, or when the user steps away from the computer temporarily. A well-chosen shortcut facilitates efficiency and promotes a sense of security. Its availability enhances the overall security posture of the user, offering a practical and immediate countermeasure against unwanted intrusions.
This discussion focuses on the technical aspects and utility of the screen-locking shortcut on macOS. Further exploration might delve into alternative security measures, such as password protection, or configurations for heightened security.
macOS Lock Shortcut
Efficient screen locking is crucial for protecting sensitive data on macOS. Understanding the essential components of the lock shortcut is paramount for optimal security.
- Security
- Convenience
- Keystroke
- Password (optional)
- Application state
- macOS version
- Data protection
A macOS lock shortcut enhances security by immediately minimizing applications and obscuring the screen, deterring unauthorized access. Convenience comes from the quick lock-unlock cycle; a well-chosen keystroke is a key component. Optional password input adds another layer of protection. Important to consider that the application state might differ based on the shortcut and user's settings. Depending on the macOS version, the specific shortcut could change. The ultimate goal is to safeguard the sensitive data stored on the machine, which a proper locking process accomplishes. For example, the shortcut might immediately safeguard open documents, while other aspects might influence the locking behavior.
1. Security
Security is a fundamental component of any operating system, particularly in the context of safeguarding sensitive information. A macOS lock shortcut plays a crucial role in this security framework. The shortcut acts as a rapid defense mechanism, instantly minimizing active applications and obscuring the screen, thereby preventing unauthorized access to data. This immediate response to potential threats is crucial for preventing both casual intrusion and more sophisticated attacks. Real-world scenarios demonstrate the value of such a system; consider a laptop left unattended in a public space. A designated lock shortcut prevents accidental disclosure of sensitive information. Such an action significantly mitigates risks in a variety of situations.
The importance of the lock shortcut extends beyond physical environments. Digital security also benefits from immediate access to this function. The potential for unauthorized access to files, accounts, and sensitive data is a continuous risk, compounded in scenarios with remote or shared access. In such circumstances, a swift lock mechanism minimizes the window of opportunity for malicious activity. The operational efficiency provided by a lock shortcut is therefore inherently linked to the broader security of the system and its data. The user can swiftly and effectively protect information with minimal disruption to the overall workflow.
In conclusion, the macOS lock shortcut is an essential element of a comprehensive security strategy. Its effectiveness stems from its ability to rapidly impede unauthorized access. By providing a quick response mechanism, the shortcut fosters a more secure digital environment. Understanding this connection is paramount for maintaining digital well-being and data protection in the modern digital age.
2. Convenience
The integration of a macOS lock shortcut enhances user experience by facilitating rapid security measures. This convenience stems from the shortcut's ability to quickly secure the system, minimizing potential disruptions or vulnerabilities during transient periods, such as brief absences or transitions between tasks. This aspect is crucial in optimizing workflow and minimizing interruptions.
- Minimizing Workflow Interruptions
A readily accessible lock shortcut minimizes the need for extended security procedures. The swift action of locking the screen allows for uninterrupted transitions between tasks or brief pauses. Users can rapidly protect the system from potential unauthorized access, maintain focus, or step away from their workstation without compromising security. This uninterrupted workflow streamlines operations, particularly in demanding or time-sensitive environments.
- Enhanced Productivity
By quickly locking the screen, users minimize the risks associated with unattended access to potentially sensitive information. This seamless integration of security into the workflow ultimately enhances overall productivity. Users do not require complex or time-consuming steps to secure their system, allowing them to maintain a focused and uninterrupted workflow. Consequently, this convenience translates to greater efficiency and decreased downtime.
- Improved System Security (indirectly)
The ease of use inherent in the macOS lock shortcut indirectly contributes to improved system security. When a lock shortcut is readily available, users are more likely to utilize it regularly. This consistent practice strengthens the system's overall security posture and reinforces a habit of protection, effectively bolstering the security paradigm. Users will be more diligent in leveraging security measures because these measures are readily available, resulting in fewer security vulnerabilities.
The convenience afforded by a macOS lock shortcut directly impacts the overall user experience and indirectly strengthens the system's security posture. This balance between security and usability is critical in maximizing user adoption and minimizing security risks. This seamless integration benefits users in various contexts, from individual work environments to more extensive organizational settings. The convenience of the shortcut enhances the operational security of the entire system, enabling better protection against unauthorized access.
3. Keystroke
The keystroke, a fundamental element in a macOS lock shortcut, defines the precise combination of keyboard presses required to activate the screen-locking function. This combination, often a sequence of specific keys, dictates the mechanism for securely locking the macOS system. Properly understanding this component is crucial for both user efficiency and overall security.
- Specificity and Security
The precise nature of the keystroke ensures only authorized users can trigger the lock function. This specificity serves as a crucial security measure, preventing accidental or unauthorized activation. The complexity of the keystroke, while seemingly simple, is vital to deter unintended or malicious activation. Variations in keystroke definitions between macOS versions underscore the need to understand the specific requirements for the targeted operating system.
- Operational Efficiency
An efficiently designed keystroke enhances user productivity. A short, memorable sequence, easily recalled, streamlines the security process. This ease of use reduces the time required to secure the system, maximizing user workflow. Conversely, a cumbersome or intricate keystroke sequence can be a substantial source of frustration and potentially affect the system's overall operational security. The ease and speed with which a user can enact the lock function strongly influences their ability to conduct tasks effectively.
- Compatibility and Context
The keystroke's implementation must align with the broader macOS architecture. Compatibility across various macOS versions and applications is critical. The keystroke sequence should not conflict with system shortcuts, preventing unexpected actions or disruptions. In specific contexts, a keystroke designed to lock might need to be different depending on the status of other functions. The ability to execute the lock action without triggering unforeseen consequences ensures the functionality of the operating system and user experience.
- Maintaining Integrity
The consistent application of the keystroke throughout the operating system ensures the integrity of the lock function. Variations in implementation, whether accidental or deliberate, can compromise security and disrupt the seamless execution of the security protocol. A carefully designed and implemented keystroke sequence ensures uniformity and reliability, maintaining the anticipated and secure locking functionality. The keystroke's consistency across the operating system is critical to the user's trust in the security mechanism.
Ultimately, the keystroke's role in a macOS lock shortcut is multifaceted. The specific combination, when properly implemented, provides a secure and user-friendly mechanism for protecting the system. From the perspective of security, the keystroke ensures only authorized users can initiate the locking procedure, enhancing the overall protection against unauthorized access. From the perspective of operational efficiency, the keystroke minimizes disruptions to the workflow, maximizing productivity. These multifaceted elements illustrate the crucial link between the keystroke and the successful implementation of a macOS lock shortcut.
4. Password (optional)
The inclusion of a password as an optional component of the macOS lock shortcut significantly enhances the system's security posture. While a shortcut itself provides a basic level of protection by obscuring the screen and minimizing applications, the optional password adds a crucial layer of defense, preventing unauthorized access even after the visual lock is engaged. This layered approach is vital in mitigating risk.
The practical significance of this optional password component is evident in various scenarios. A user working on sensitive documents, an organization handling confidential data, or an individual in a shared work environment benefits from this extra safeguard. If a device is misplaced or stolen, the password acts as an additional barrier, preventing unauthorized individuals from accessing the protected information. Conversely, in situations where a user only requires a temporary lock, such as leaving their workstation for a few minutes, a password is unnecessary and the lock shortcut can effectively secure the device immediately. This flexibility highlights the crucial balance between security and accessibility.
In essence, the optional password component, when integrated with the macOS lock shortcut, creates a more robust security architecture. It underscores the importance of considering varying user needs and contexts while designing security protocols. The ability to tailor security measures to specific requirements ensures a practical application that prioritizes security without compromising user convenience. Understanding this interconnectedness is paramount for both individual users and system administrators seeking to optimize security practices.
5. Application State
The application state directly influences the efficacy of a macOS lock shortcut. The state of running applications significantly impacts how the lock function operates. A crucial aspect of the lock shortcut is its ability to ensure that all applications are either minimized or shut down when the system is locked. This action prevents potential unauthorized access to data or actions in open applications. For instance, if an application remains open and active, sensitive data might still be accessible, even after the screen lock is engaged. This inherent link between application state and security mechanisms highlights the importance of a lock function that addresses application activity.
The practical implications of understanding application state within the context of a macOS lock shortcut are substantial. A functioning lock mechanism should handle diverse application states effectively. Consider a user working on a spreadsheet containing sensitive financial data. An improperly implemented lock shortcut might not immediately minimize or close the application, potentially exposing the data if the computer is left unattended. Conversely, a well-designed shortcut will immediately minimize or close the application, preventing unauthorized access. This consideration extends beyond individual use; in shared work environments or public access points, safeguarding application states during temporary absences or public use becomes critical to maintain confidentiality. Therefore, effective protection requires not only the quick lock function but also the consideration of the application state within that process.
In conclusion, the application state is a critical component in the design and implementation of a macOS lock shortcut. A well-structured lock function should account for the various application states. This consideration directly impacts the overall security posture of the system and its ability to effectively protect sensitive data. Understanding the correlation between application state and the lock shortcut's functionality is essential for ensuring data security and protecting sensitive information in diverse operational contexts, including but not limited to individual use, shared access points, and public workstations.
6. macOS Version
The macOS version significantly influences the availability and functionality of the screen-locking shortcut. Variations in operating system releases often introduce modifications to core system functions, including the screen-locking mechanism. Understanding these changes is critical for ensuring effective security and compatibility.
- Compatibility and Functionality
Different macOS versions may implement the screen-locking shortcut differently. A shortcut that works in one version might not function identically in another. For example, a key combination used in macOS Mojave might require adjustment in macOS Monterey. This necessitates a user's awareness and adaptation based on the macOS version.
- Security Enhancements and Changes
macOS updates often incorporate security enhancements. These changes can impact the screen-locking mechanism, potentially altering the shortcut itself or introducing new security features. Users need to account for these updates, as a shortcut that was adequate in a previous version might no longer be the optimal choice in a more advanced operating system.
- Keystroke Differences
Specific keystrokes used for the screen-locking shortcut can vary across macOS versions. Understanding the keystroke associated with each macOS version is necessary for maintaining consistent security procedures. A key combination that reliably locked the screen in an earlier version might not function in a later release. Therefore, proper training and updates to instructions are paramount.
- Hidden or Changed Features
Certain macOS versions may introduce or remove hidden features that influence the lock shortcut's behavior. Unknown changes to the lock mechanism can have unexpected repercussions. For instance, the lock might operate differently concerning application management in subsequent versions, potentially requiring a user to understand the application's impact on the security function. Keeping abreast of official documentation is essential.
In summary, the specific macOS version directly impacts the macOS lock shortcut's usability and security. Users should maintain awareness of these changes through official documentation and updates, which ensure a consistent and effective security protocol. Keeping up-to-date with the latest macOS versions provides the most secure and reliable screen-locking functionality. Understanding the correlation between macOS versions and the lock shortcut is fundamental for maintaining optimal system security and operational efficiency.
7. Data Protection
Data protection is paramount in the digital age. A macOS lock shortcut plays a significant role in this area. Proper implementation of this shortcut directly impacts the security and integrity of stored data. The effectiveness of the shortcut depends on the level of data protection it provides, which this section will explore.
- Preventing Unauthorized Access
A primary function of the macOS lock shortcut is to impede unauthorized access to sensitive data. This involves minimizing active applications and obscuring the screen. The immediate nature of this action helps prevent casual viewing or accidental exposure of confidential information, especially in shared or public environments. This functionality has implications for personal data, financial transactions, and confidential documents. Unauthorized access can lead to data breaches and potential financial or reputational damage.
- Mitigation of Casual Data Exposure
The lock shortcut serves as a basic but crucial defense against accidental or inadvertent disclosure of data. A user briefly stepping away from their device might expose sensitive information if no security measures were in place. This is particularly relevant in shared workspaces or public areas. The shortcut mitigates this risk by quickly obscuring the display and minimizing applications, reducing the window of vulnerability for unauthorized viewing.
- Enhancement of Data Integrity
By quickly locking the screen, the shortcut actively contributes to the integrity of data. Unauthorized modifications or alterations to the data are significantly curtailed. The instant nature of the locking action is crucial, preventing unwanted interventions or changes while the computer is unattended. The protection against such breaches ensures that the data remains accurate and reliable, preventing potential loss or corruption.
- Contextual Security Considerations
The effectiveness of data protection through a lock shortcut is also contingent upon contextual factors. For instance, if a computer is in a public area or is a shared system, the lock shortcut plays an especially crucial role. This contextual awareness emphasizes the need to use the appropriate security measures for the surrounding environment. Factors such as physical security measures, user awareness, and the sensitivity of the data must all be considered.
In conclusion, data protection is intrinsically linked to the functionality of a macOS lock shortcut. The shortcut's effectiveness in preventing unauthorized access, mitigating accidental exposure, and enhancing data integrity is crucial. By understanding the interplay between these elements, users can optimize data protection measures and safeguard sensitive information in various contexts.
Frequently Asked Questions about macOS Lock Shortcuts
This section addresses common inquiries regarding macOS lock shortcuts, providing concise and informative answers to enhance understanding and usage.
Question 1: What is the purpose of a macOS lock shortcut?
A macOS lock shortcut serves to rapidly secure the system. This involves minimizing active applications and obscuring the screen, thereby deterring unauthorized access. This action is crucial for preserving data integrity and preventing accidental or malicious use.
Question 2: How does the lock shortcut differ from a password?
While a password provides a further layer of security by requiring authentication, a lock shortcut offers immediate protection against casual access. The shortcut addresses the potential exposure of sensitive data during brief absences, whereas the password ensures only authorized users access the system. Both mechanisms are essential elements of a comprehensive security approach.
Question 3: Are there variations in the lock shortcut across macOS versions?
Yes, macOS versions may employ different keystroke combinations for the lock shortcut. Consulting system documentation or resources specific to the macOS version in use is crucial for accurate implementation and functionality.
Question 4: Does the lock shortcut automatically close all running applications?
The behavior of the lock shortcut regarding application closure can vary. Some shortcuts may minimize open applications, while others might close them entirely. Referencing macOS documentation for the precise implementation in the current version is essential to ensure expected behavior.
Question 5: How can the lock shortcut enhance data security in a shared environment?
In shared environments, the lock shortcut provides immediate protection against unauthorized access to sensitive data or potential disruption. Its use significantly mitigates the risk of accidental or intentional disclosure. Combined with other security measures, it forms a robust defense mechanism for sensitive information.
Understanding the proper use of macOS lock shortcuts is paramount for safeguarding data and maintaining system security. The shortcut is a critical component of a comprehensive security strategy, but should be used in conjunction with other security measures.
This concludes the Frequently Asked Questions section. The next section will delve into the technical aspects of implementation and configuration.
Conclusion
This exploration of the macOS lock shortcut highlights its multifaceted importance in modern digital security. The shortcut's primary function is rapid system security, minimizing risks associated with unattended access to sensitive data. Key aspects, such as the keystroke combination, application state handling, and macOS version compatibility, significantly influence the shortcut's effectiveness. The optional password component enhances security further, creating layered protection. Understanding the interplay between these elements is crucial for optimal system security and user experience. The convenience and speed of the shortcut directly impact workflow efficiency, fostering a balance between security and productivity.
Effective use of the macOS lock shortcut remains a critical aspect of maintaining a secure digital environment. Maintaining awareness of evolving macOS versions and the associated changes in functionality is essential. Continuous vigilance and adaptation to security best practices will be vital in a rapidly evolving digital landscape. This approach will, in turn, help to safeguard data and maintain system integrity. The effective integration of such a shortcut is a demonstrably crucial component of a broader security strategy. The shortcut's effectiveness relies heavily on its correct implementation and understanding, underscoring the importance of proactive security measures.
You Might Also Like
Frankie Pulitzer: Amazing New Music!Brokeback Mountain Filming Locations: Where The Story Unfolded
Matt James Final 2: Love, Loss, & The Next Chapter
Crisco History: From 1911 To Today's Kitchen
Jack Dorsey's Drake Connection: Unveiling The Story
Article Recommendations
- 1955 Quarter Value How Much Is Your Coin Worth
- Augment R Your Aipowered Solution
- Michael Marchetti Top Insights Strategies