How to quickly secure a macOS device? A dedicated approach to screen locking on Macs.
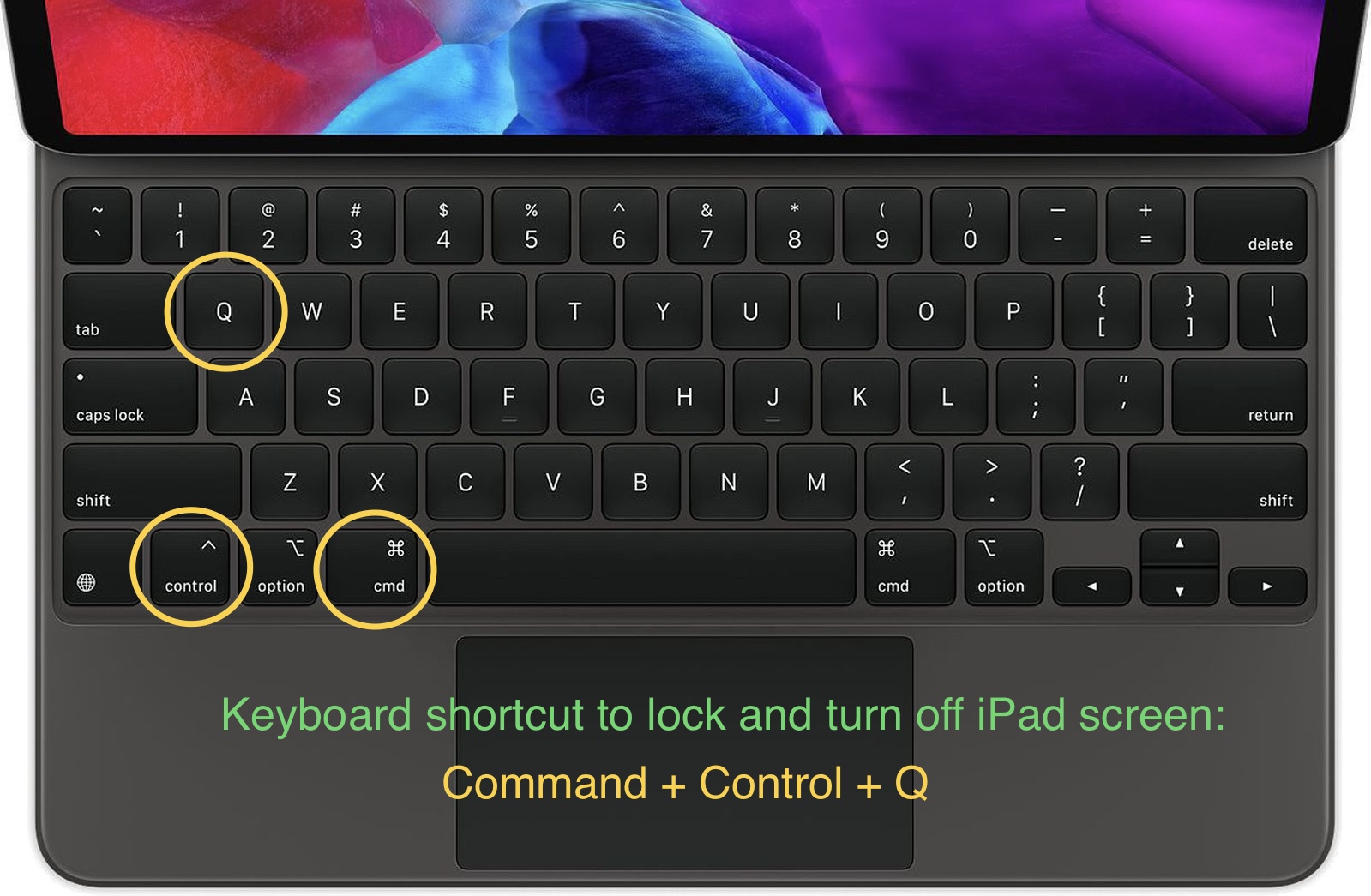
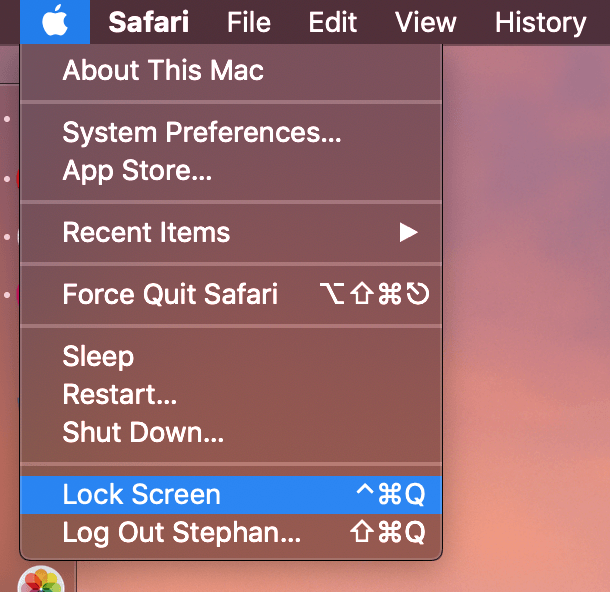
This feature facilitates rapid access to a secure screen. It enables users to lock the computer's display by initiating a predefined action, typically a keyboard combination or mouse click. For instance, pressing Command + Control + Q or using a dedicated button or menu option might trigger the lock screen. This method replaces the more cumbersome method of using the password to lock the display.
The benefits of such a shortcut are manifold. Time saved is a significant advantage, especially in situations requiring quick transitions between tasks or when securing the computer in public areas. Moreover, a readily accessible method ensures consistent security measures. This is crucial for maintaining data protection and system integrity. The practice of locking a computer is crucial for maintaining privacy and preventing unauthorized access.
Let's now explore various strategies for implementing and optimizing this feature on modern macOS systems.
macOS Lock Screen Shortcuts
Efficient screen locking is paramount for safeguarding sensitive data on macOS. Effective shortcuts streamline this process, enhancing security and user experience.
- Keyboard Combinations
- Quick Access Buttons
- Security Enhancements
- Accessibility Options
- System Settings
- Public Use Considerations
- Privacy Implications
- Performance Optimization
Keyboard shortcuts like Command+Control+Q offer rapid locking. Quick access buttons, often integrated into the menu bar, provide a second method for immediate action. Security enhancements inherent in these shortcuts provide additional protection. Accessibility options ensure users with various needs can employ these features. System settings allow customization, adjusting shortcut configurations. Public use situations necessitate a well-configured lock screen shortcut. Privacy implications underscore the importance of a well-placed locking mechanism. Performance optimization, like ensuring smooth access to locking, is essential for a seamless user experience. These features combined result in a system that is both secure and user-friendly.
1. Keyboard Combinations
Keyboard combinations are fundamental to macOS lock screen shortcuts. These combinations, often a specific sequence of keys, provide rapid access to the lock screen, offering a time-saving and secure alternative to other methods. Their effectiveness depends on accessibility and memorability, which influence user experience and security protocols.
- Accessibility and Design
Effective keyboard combinations must be easily accessible and logically assigned. This prioritizes usability, especially for users with diverse needs and experience levels. The design principles for keyboard shortcuts, including the choice of keys, should account for the frequent use and promote memorization. Unnecessary complexity should be avoided to prevent user frustration or errors. Good design is crucial to the effectiveness of a shortcut.
- Security Considerations
The security implications of keyboard shortcuts are significant. Appropriate key combinations should be chosen to prevent accidental activation or unintended access to sensitive settings or data. The design process should incorporate robust security measures to prevent unauthorized screen locking or bypasses. Strong, unique combinations limit the possibility of compromised security through predictable keystroke patterns.
- Efficiency and User Experience
Optimized keyboard combinations enhance user efficiency. Quick and reliable access to the lock screen improves productivity and reduces downtime. The design considerations for the shortcuts directly influence user experience. The chosen combinations should be intuitive and consistent with typical macOS keyboard navigation practices to minimize user frustration and maximize adoption.
- System Integration
Keyboard combinations for lock screen access must integrate seamlessly with the broader macOS system. Integration ensures consistent behavior across various applications and software components. The combination should be robust enough to function correctly even under pressure or unusual circumstances, preventing unexpected crashes or system errors.
In summary, effective keyboard combinations for macOS lock screen shortcuts prioritize usability, security, and efficiency. Thoughtful design and integration with the macOS environment are crucial for creating secure, efficient, and user-friendly access to the lock screen.
2. Quick Access Buttons
Quick access buttons, often integrated into the macOS menu bar or system tray, offer a supplementary method for initiating a lock screen shortcut. This direct approach complements keyboard combinations, providing an alternative pathway to quickly secure the system. The integration of these buttons with existing operating system interfaces emphasizes their role in enhancing user experience and security.
- Placement and Visibility
Strategic placement of these buttons within the macOS user interface is crucial. Prominent and easily accessible locations, such as the menu bar, improve the likelihood of their use. Conversely, obscure placements diminish their utility, potentially reducing the efficacy of the lock screen shortcut. The visual design and color scheme should be aligned with macOS conventions, ensuring seamless integration and consistency.
- Functionality and Triggering Mechanism
These buttons should directly and reliably trigger the lock screen shortcut without undue complexity or ambiguity. The triggering mechanism, be it a single click or a combination with other actions, must be user-friendly and intuitive. Clear visual feedback, such as a subtle change in the button's appearance, confirms successful activation of the shortcut. The mechanism should ensure that any actions beyond a basic click are straightforward.
- Contextual Relevance
Placement and function should reflect the context of their use. The relevance of a quick access button for locking the screen is stronger when situated in areas where security concerns are paramount. For example, proximity to a power button, a logout icon, or the notification area enhances the contextual appropriateness and user expectations. The contextually relevant placement improves both usability and efficiency.
- Integration with Other macOS Features
The seamless integration of quick access buttons with other macOS features, like screen savers or system-wide notifications, enhances user experience. A well-integrated button ensures the system behaves predictably and consistently. Incorporating a visual cue or feedback during the locking process maintains a user-friendly experience. The integration helps in reducing any potential user confusion or technical issues.
In conclusion, quick access buttons provide an alternative and often preferable means for launching the lock screen shortcut. Their strategic placement, effective triggering, contextual relevance, and seamless integration with other macOS features are vital for usability, efficiency, and security. Consistent implementation of these buttons elevates the user experience by streamlining the security protocols within the macOS environment.
3. Security Enhancements
Security enhancements are intrinsically linked to the effectiveness of a macOS lock screen shortcut. A robust shortcut, effectively implemented, strengthens the overall security posture of the system. The connection lies in the shortcut's ability to quickly and reliably initiate a secure state, preventing unauthorized access. This document explores key aspects of this interplay, focusing on the practical application and implications within the macOS environment.
- Password Protection Integration
The lock screen shortcut's primary function is to initiate a secure state. This requires integration with password protection. The system must ensure that access is only granted after the correct password is input. This linkage is critical, as a shortcut without robust password validation would effectively render the locking mechanism useless. Examples include the validation process before any actions requiring administrator privileges or sensitive data access.
- Time-Based Locking and Idle Timeout
Time-based locking and idle timeouts, combined with the shortcut, provide an additional layer of security. These features, frequently integrated with lock screen shortcuts, automatically lock the system after a period of inactivity. This automatically locks the screen if the computer is left unattended. Thus, if unauthorized access is attempted during this idle time period, the locking mechanisms will already be in place.
- Multi-Factor Authentication (MFA) Integration
Integration with MFA adds an additional layer of complexity to the security. A successful lock screen shortcut should incorporate MFA to restrict access further. This enhancement involves requiring multiple forms of verification, such as a security code sent to a secondary device, to authenticate the user and prevent unauthorized access when the system is locked. This substantially strengthens the security protocol.
- Data Encryption and Protection
Data encryption, alongside the lock screen, encrypts the sensitive data stored on the computer. The lock screen shortcut, when paired with secure encryption protocols, ensures that sensitive data remains confidential and secure. This prevents unauthorized access, even if the computer is compromised. The lock screen acts as a critical barrier, safeguarding against access to sensitive data. Thus, a secure lock screen, combined with encryption, provides a comprehensive security shield.
In conclusion, effective security enhancements tightly interweave with a lock screen shortcut. A well-designed shortcut, when integrated with measures like password protection, time-based locking, MFA, and robust encryption, forms a powerful security framework. This combination safeguards sensitive data and prevents unauthorized access to the system, emphasizing the importance of holistic security measures within the macOS operating system.
4. Accessibility Options
Accessibility options are integral to the usability and effectiveness of a macOS lock screen shortcut. Their importance stems from the need to cater to diverse user needs and ensure inclusivity. A well-designed lock screen shortcut should accommodate various abilities, including visual impairments, motor disabilities, and cognitive differences. Failure to consider these options can hinder the accessibility of the lock screen for a significant portion of the user base.
Practical examples illustrating this connection abound. A user with limited dexterity might rely on voice control or alternative input methods. A screen reader user requires the lock screen interface to be properly structured for screen reading software to interpret the elements, including buttons, fields, and instructions. A user with cognitive differences might benefit from simple, uncluttered interfaces with clear visual cues and simple navigational patterns. These considerations underpin the need for lock screen shortcuts that accommodate varying needs. Failure to incorporate such accommodations can significantly limit the utility of the lock screen shortcut, affecting both individual user experience and the overall system accessibility.
Understanding the connection between accessibility options and macOS lock screen shortcuts is crucial for creating inclusive and user-friendly systems. A well-designed shortcut, mindful of these considerations, promotes a more comprehensive and equitable approach to system use. This understanding ensures that security measures do not compromise user experience and that the lock screen serves its intended purpose without excluding portions of the user population. Ignoring this vital connection potentially leads to a system that is less usable for a significant portion of its users.
5. System Settings
System settings play a critical role in configuring and managing macOS lock screen shortcuts. These settings act as the control panel for various aspects of the lock screen's behavior. The link between system settings and lock screen shortcuts is fundamental. System settings dictate how the lock screen shortcut functions, encompassing elements like the triggering mechanism, security protocols, accessibility options, and more. Without appropriate configurations in system settings, the lock screen shortcut may not operate as intended, rendering it ineffective or even unsafe.
Specific settings directly influence the lock screen shortcut's behavior. For instance, the choice of keyboard combination for the shortcut is configured within system settings. Similarly, the idle timeout period, determining when the screen automatically locks, is also managed through system settings. Accessibility settings related to voice control or screen reader integration directly impact how users with disabilities interact with the lock screen shortcut. The security protocols associated with password complexity, two-factor authentication, or encryption are also part of these settings, illustrating the critical dependence of the lock screen shortcut on system configurations. Real-world implications arise from the proper use of these settings; a poorly configured system setting could impede security or make a lock screen shortcut inaccessible to a user. System settings, therefore, are not merely supporting components; they are the core determinants of the lock screen shortcut's practicality and security.
Understanding the intricate relationship between system settings and lock screen shortcuts is essential for maintaining a secure and accessible macOS environment. Proper configuration ensures that the shortcut serves its intended purposeproviding a convenient and secure method for locking the screen. System settings, therefore, serve as a crucial interface for managing and optimizing the lock screen shortcut, underscoring their importance for comprehensive security and usability. This understanding is vital for anyone managing or configuring macOS systems, as well as for users seeking to tailor their security settings for optimal use.
6. Public Use Considerations
Public use environments necessitate heightened security awareness. A robust lock screen shortcut becomes crucial in such settings. The quick access to a secure screen, enabled by the shortcut, directly addresses the increased risk of unauthorized access prevalent in public spaces. This becomes especially important when the device is left unattended or in shared environments. A dependable lock screen shortcut, readily accessible and seamlessly integrated into the operating system, ensures rapid security measures, directly mitigating the vulnerability to potential misuse.
Practical examples illustrate this connection. A shared computer in a library or a public workstation in a coffee shop presents a higher risk of unauthorized access compared to a personal computer at home. A robust lock screen shortcut is paramount to quickly secure sensitive information when leaving the workstation. The shortcut's function is even more significant in a public place. Quick locking mechanisms, whether keyboard combinations or dedicated buttons, can prevent access to data while the device is out of use. The security benefits are immediately apparent, especially given the increased risk of malicious intent in public spaces. The need for a well-designed, reliable shortcut is evident in situations where the safety of data is paramount.
In summary, understanding the connection between public use considerations and a macOS lock screen shortcut is essential for effective system security. The rapid initiation of a secure lock screen, as provided by a well-designed shortcut, directly addresses the heightened security risks present in public environments. This understanding underscores the necessity for a lock screen shortcut that seamlessly blends convenience with robust security, ensuring that data remains protected in potentially risky situations. Failing to consider public use scenarios can compromise the security of sensitive information and the user's privacy.
7. Privacy Implications
A macOS lock screen shortcut, while seemingly a simple convenience, carries significant privacy implications. Its effectiveness hinges on the understanding of how access to the device is managed. A poorly implemented or inadequately secured shortcut can undermine the overall privacy protections offered by the operating system. The proper functioning of the shortcut is inextricably linked to the privacy of the user's data and personal information.
The security of sensitive data relies heavily on the reliability of the locking mechanism. A compromised shortcut could potentially grant unauthorized access to the system, jeopardizing personal information, financial data, or confidential communications. For example, a vulnerable shortcut that can be bypassed might enable malicious actors to access stored documents, emails, or sensitive applications. Furthermore, the design of the shortcut influences the privacy of data during transitions between users, particularly in shared workspaces or public settings. A user leaving a device in an unsecured public area risks exposing their data unless the lock screen shortcut is adequately secured. Effective implementation of the shortcut, paired with robust security measures like strong passwords and multi-factor authentication, minimizes potential privacy breaches.
Consequently, a thorough understanding of the interplay between privacy implications and the lock screen shortcut is critical for maintaining data security. Failing to appreciate these implications can lead to significant privacy violations. The shortcut must be viewed as an integral component of the broader security strategy rather than merely a convenience. This perspective emphasizes that the lock screen shortcut's function extends beyond basic screen protection. It plays a crucial role in safeguarding user privacy within the context of the wider macOS ecosystem. Appropriate configuration and maintenance of the shortcut contribute substantially to upholding the privacy standards expected in modern computing environments.
8. Performance Optimization
Performance optimization is intrinsically linked to a macOS lock screen shortcut's efficacy. A sluggish or inefficient shortcut negatively impacts user experience and potentially the overall system responsiveness. A fast, smooth transition to the locked screen and subsequent unlocking is crucial. The speed at which the lock screen shortcut executes, and the responsiveness of the system afterward, directly affects the user experience and, by extension, productivity. Optimizing this process ensures a seamless workflow. Examples include a user accessing a presentation, quickly locking the screen to protect their work and then smoothly returning to their task, or a remote employee logging into a workstation remotely, needing instant lock-screen access to maintain data security. A slow shortcut can disrupt tasks and potentially introduce security vulnerabilities due to delays.
Several factors contribute to the performance optimization of lock screen shortcuts. Efficient code execution is paramount. Minimizing unnecessary processes during activation and unlocking phases is essential to prevent performance bottlenecks. Reducing resource consumption is equally important, minimizing strain on CPU, memory, and graphics processing. Optimized algorithms for display updates, authentication checks, and secure screen lock procedures are integral. Minimizing background processes during the locking action improves responsiveness. Well-structured code, reducing complex calculations or lengthy operations during shortcut execution, enhances performance. Testing and benchmarking are vital to identify and address performance bottlenecks. Thorough testing under varying system loads allows for targeted optimization to maintain consistency under different circumstances. This proactive approach avoids slowdowns in public areas or during peak usage, critical for a smooth user experience.
In conclusion, the performance characteristics of a macOS lock screen shortcut are paramount for usability and user satisfaction. Efficient execution, optimized resource management, and well-structured code are critical components. Proper performance optimization, therefore, is not merely a technical concern but a key element in creating a user-friendly and secure system. This approach ensures a positive user experience, enabling smooth transitions between tasks and enhanced security, ultimately enhancing overall system usability and reliability. Addressing performance considerations within the context of the lock screen shortcut is crucial for establishing a system that is both secure and responsive.
Frequently Asked Questions
This section addresses common queries regarding macOS lock screen shortcuts, providing clear and concise answers to frequently encountered questions.
Question 1: What are the primary functions of a macOS lock screen shortcut?
A macOS lock screen shortcut's primary function is to swiftly secure the computer by initiating the lock screen. This provides a convenient way to protect sensitive information and prevent unauthorized access, especially when temporarily leaving the device unattended.
Question 2: What keyboard shortcuts are commonly used for locking the screen?
Common keyboard shortcuts include Command + Control + Q. Other keyboard combinations might be customized within system settings.
Question 3: How can I customize my lock screen shortcut settings?
Customization options for lock screen shortcuts are typically found within the macOS System Preferences. Users can adjust keyboard combinations, idle timeouts, and other settings based on individual requirements and preferences.
Question 4: Are there accessibility options available for lock screen shortcuts?
Yes, macOS offers accessibility options to tailor lock screen shortcuts to various user needs and preferences. These settings might include voice control, alternative input methods, or integration with screen readers for users with disabilities.
Question 5: Why is optimizing lock screen shortcut performance important?
Optimizing lock screen shortcut performance ensures a smooth and responsive user experience. Slow or inefficient shortcuts can disrupt workflow and potentially introduce security vulnerabilities due to delays in locking the device.
In summary, macOS lock screen shortcuts offer a convenient and secure method for protecting sensitive information. Customization, accessibility options, and performance optimization are essential for a streamlined and user-friendly experience. Users should familiarize themselves with these features to maximize the benefits and security features of their macOS devices.
Proceed to the next section for detailed instructions on configuring and optimizing lock screen shortcuts.
Conclusion
This exploration of macOS lock screen shortcuts highlights the multifaceted nature of this seemingly simple feature. The study demonstrates the crucial role of these shortcuts in maintaining system security and user experience. From keyboard combinations and quick access buttons to security enhancements and accessibility options, the efficacy of a lock screen shortcut hinges on its integration with various system settings and functionalities. Public use considerations and privacy implications underscore the need for robust design choices. Performance optimization is essential for seamless operation and a positive user experience. These interconnected elements contribute to a secure and dependable system, emphasizing the significance of appropriate configuration for optimal usage within the macOS environment. Understanding the relationship between these factors provides a framework for secure and user-friendly device management.
Moving forward, continued development of macOS lock screen shortcuts should prioritize user needs and safety concerns. Robust accessibility features, seamless integration across applications, and continual optimization for performance are critical. These enhancements are vital for maintaining data security and promoting a positive user experience within the dynamic and ever-evolving macOS landscape. The effective implementation of lock screen shortcuts serves as a vital layer of protection in a digital environment and enhances the overall security posture of a macOS system.
You Might Also Like
Toledo Zoo Experience Package: Unforgettable Fun!Evan Peters & Halsey: Hot New Couple?
Unlocking The Power Of ReTsu DAO: A Deep Dive
Lamonica Garrett Parents: Who Are They?
Pit Boss Vs Traeger: Which Pellet Grill Is Right For You?
Article Recommendations
- George Sakellaris Inspiring Stories Insights
- Bill Emerson Bridge History Facts
- Best Led Qr Codes For Your Project Display